After running wireshark, start a capture on your interface connected to the Internet (usually eth0 or something like that), then set a filter (a regular filter in the main window, not a capture filter in the capture options menu) of udp.port == 53. After doing this, ping www.hawaii.edu.
How many queries were sent by your host?
What kinds of queries did your host send?
How many responses did your server send?
Please note: sniffing tools such as wireshark can be used for malicious purposes as well as for network debugging. If we learn that, while you are enrolled in this class, you have used wireshark to obtain others' information without their consent, you will fail the class (get a grade of F -- see also the note on cheating near the end of this page). If done at UH, you would also be in violation of UH policy 2.210, Use and Management of Information Technology Resources.
Also note that your system may be making DNS requests independently of any activity on your part. In the answers to the questions above, please focus only on the DNS packets exchanged for the ping.
All users have the responsibility to operate the University computing systems in an ethical, lawful and responsible manner.
b. Users must respect the privacy of others’ passwords, information and communication,
The client should take as its first (or only) command-line parameter a domain name. The domain name may or may not be an FQDN, that is, terminated by a '.'. In other words, your client should be able to correctly send requests for www.hawaii.edu and also www.hawaii.edu.
The client should also accept an optional second parameter, which is the IP address of a domain name server. The second parameter is optional on the command line -- your code MUST implement it. If the server is not specified, use 127.0.0.1, which is your local host. Use inet_aton or inet_pton in your code to convert the second parameter, if any, to an IP number. If you wish, you may use the following code.
int port = 53;
struct sockaddr_in sin;
sin.sin_family = AF_INET;
if (! inet_aton (server, &(sin.sin_addr))) {
printf ("invalid server IP %s\n", server);
exit (1);
}
sin.sin_port = htons (port);
The client should open a socket, build a DNS request for the given domain name, and sendto the request to the server. The client should then sleep(2) (have your code sleep for 2 seconds) to give the server time to reply (for now, the reply is ignored) and then close the socket.
This process (sending a DNS request) should be repeated three times, once to request the A record, once for the AAAA record, once for the MX record.
You may either (a) open a socket, send a request, sleep, close the socket, and repeat the process three times, as described above, or (b) open the socket, send three requests, sleep, and close the socket.
To show that your code works, send the requests using your local IP address (127.0.0.1) as the server, and look at the result on wireshark. The result should resemble the following.
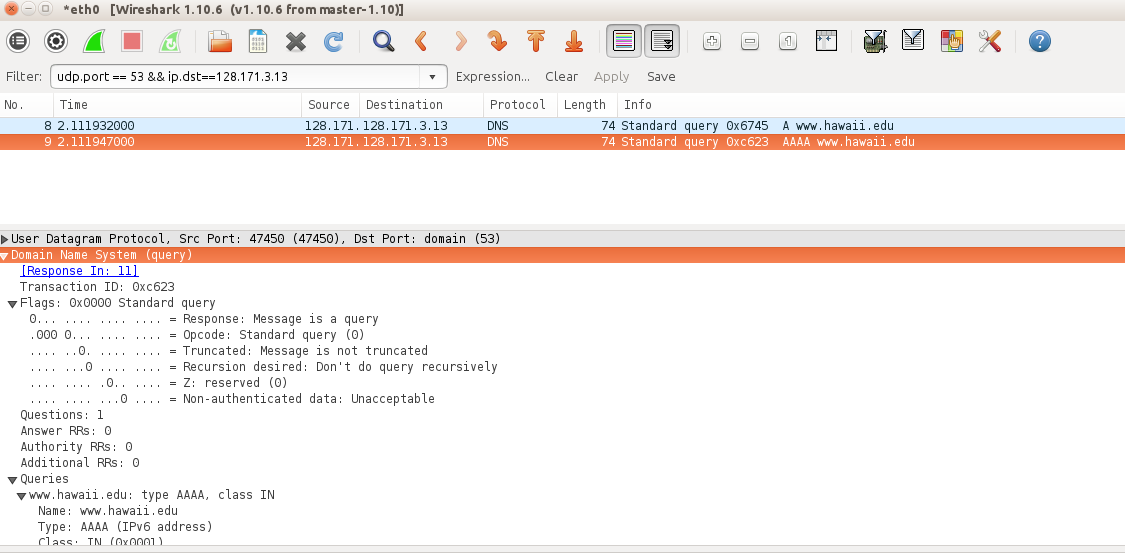

Turn in your code and a screenshot showing that wireshark does not report any errors for your packets.
You may see in wireshark ICMP packets reporting that the port is unreachable on your host -- you may ignore those packets (they simply report that there is no DNS server running on your system). Any other errors must be corrected before you attempt the next part.
Also note that the DNS queries sent by your client will differ subtly from the queries sent by most clients, which use EDNS (Extended DNS).
Information about DNS is available in the textbook, in the instructor's notes for January 29th, in RFC 1035 (type AAAA is defined in RFC 3596 and has the numerical value 28 -- remember to use htons).
If wireshark reports that your client sends requests without errors for a variety of different domain names, send a request to a standard server such as your machine's default DNS server or UH's 128.171.3.13. If all goes well, you will get a corresponding response. Be sure to try some domain names you are familiar with, as well as some non-existent domain names.