TCP
- TCP window scaling
- TCP streams and push
- TCP header
- tcpdump and wireshark
TCP window scaling
- the window field in the TCP header is 16 bits, so the largest
window is 65,535 bytes
- this is not enough for full bandwidth on a 100ms (RTT) gigabit
ethernet, with a bandwidth-delay product of 100Mb = 12.5MB
- so TCP provides a window scaling option, sent with the
SYN packet
- the option only takes effect if both sides send a window scaling
option with their SYN packet
- if I send a window scale with a value of n, where
0 <= n <= 14, then I must divide the windows
that I send by 2n
- correspondingly, if I receive a window scale with a value
of n, then I must multiply the windows that I receive by
2n
- since n <= 14, the maximum window size is
< 230 bytes
- window scaling is defined in
RFC 1323,
"TCP Extensions for High Performance", which also provides protection
against wrapped sequence numbers.
TCP options
- TCP options may follow the basic header
- most TCP options are only sent with the SYN and SYN+ACK packet
- this picture shows options sent with a SYN
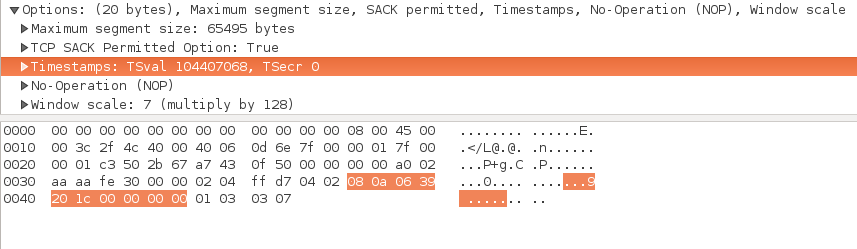
- and with the corresponding SYN-ACK
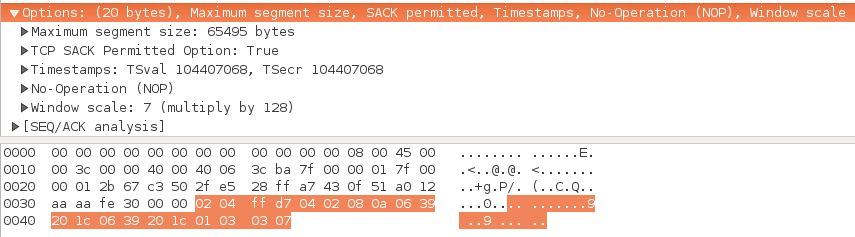
- can you guess the standard format for options?
TCP Streams and push
- TCP actually has a segmentation bit: PSH, or push
- when the application "pushes" the data, that information could be
conveyed all the way to the application at the other end
- if TCP can coalesce several user segments (each with PSH) into one
TCP segment, that TCP segment can only carry one PSH bit
- so passing PSH to the application is optional, and TCP has
no record boundaries
- so push is an advisory bit only: it encourages TCP (and the
application) to assume that the data must be sent (and presumably
replied to) before more data will be sent
TCP header
0 1 2 3
0 1 2 3 4 5 6 7 8 9 0 1 2 3 4 5 6 7 8 9 0 1 2 3 4 5 6 7 8 9 0 1
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
| Source Port | Destination Port |
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
| Sequence Number |
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
| Acknowledgment Number |
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
| Data | |C|E|U|A|P|R|S|F| |
| Offset|Reservd|W|C|R|C|S|S|Y|I| Window |
| | |R|E|G|K|H|T|N|N| |
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
| Checksum | Urgent Pointer |
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
| Options | Padding |
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
| data |
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
TCP Header Format
TCP Header fields
- Source and Destination port: demultiplexing
- Sequence and acknowledgement: reliable delivery
- Data Offset: header size, options
- Window: flow control
- Checksum: correctness
- Urgent Pointer: "special place" in the data stream
TCP Header bits
- SYN: I want to establish a connection
- FIN: I will never again send data on this connection
- RST: kill this connection
- PSH: immediate delivery of this data is probably a good idea
- URG: the urgent pointer is valid
- ACK: the acknowledgement field is valid (set in all but the
first SYN packet)
- ECE: this packet acknowledges a packet received with the IP
"congestion experienced" bit set
- CWR: the sender of this packet has reduced its congestion window
- the last two bits will be discussed in the context of congestion
control
tcpdump and wireshark
- tcpdump is a utility to look at all the packets on the network
and print out the headers
- usually run as root
- Wireshark is similar but (a) window-based, (b) newer
- Wireshark was forked from a project called Ethereal
- The pictures above, of the TCP options, are from wireshark
16:41:58.905998 maru.ics.hawaii.edu.14407 >
volcano.telnet: S 2671654129:2671654129(0)
win 512 [tos 0x10]
16:41:59.115893 volcano.telnet >
maru.ics.hawaii.edu.14407: R 0:0(0)
ack 2671654130 win 0
tcpdump example
16:47:02.285753 maru.1022 > volcano.ssh:
S 185741093:185741093(0) win 512
16:47:02.495648 volcano.ssh > maru.1022:
S 3829593384:3829593384(0)
ack 185741094 win 16352
16:47:02.495648 maru.1022 > volcano.ssh:
. ack 1 win 32120 (DF)
16:47:07.183328 volcano.ssh > maru.1022:
P 1:16(15) ack 1 win 16352 (DF)
16:47:07.183328 maru.1022 > volcano.ssh:
P 1:16(15) ack 16 win 32120 (DF) [tos 0x10]
16:47:07.433203 volcano.ssh > maru.1022:
P 16:292(276) ack 16 win 16352 (DF)
16:47:08.502673 volcano.ssh > maru.1022:
P 16:292(276) ack 16 win 16352 (DF)
16:47:08.522663 maru.1022 > volcano.ssh:
. ack 292 win 32120 (DF) [tos 0x10]



