Final Review
- IP, routing, protocol implementation
- network address translation
- transport layer, TCP, reliable transmission, flow and congestion control
- lower layers, including wireless and Aloha, Ethernet, learning
bridges, switches
- ATM and public networks
- basic issues
Internet IP Layer
- responsible for unreliable end-to-end packet delivery
- IP: header, IPv6, configuration, interface(s)
- ICMP: error reporting, problem discovery (ping, traceroute)
- SLIP: framing
- Routing: packet forwarding, RIP, OSPF, BGP
- Protocol Implementations
Network Address Translation
- NAT is nonstandard -- what is standard is using a router
- an endpoint router (gateway) does the following:
- forwards packets from the Internet to the internal network
- forwards packets from the internal network to the Internet
- does not modify the source and destination
- does not look at the higher layer (transport layer or ICMP) headers
- usually runs a routing protocol
- such a router has disadvantages for a SOHO (Small Office/Home Office):
- the IPs on the inner network must be routable, that is, recognizable
throughout the Internet and assigned to this network, which can be expensive
- IP addresses alone do not provide enough information for useful
access control
- in particular, SOHOs usually want to restrict access only to
outgoing connections and to servers known to the administrator
Network Address Translation
- a NAT box performs the forwarding functions of a router, but not
the general routing functions. In particular, the "inside" addresses
are not Internet routable addresses, e.g. are from 10.0.0.0/8,
172.16.0.0/12, or 192.168.0.0/16 (RFC 1918)

- when a NAT box with external IP number IPofficial is
forwarding a packet with the SYN bit set, it:
- in -> out: records inner IP (source IP) and inner port (TCP
source port), then rewrites the source IP number to be
IPofficial, and may rewrite the source port number to be
a port on the NAT box, PortNAT
- out -> in: checks the destination port to make sure this connection
is authorized, then rewrites the destination IP (and perhaps the destination
TCP port) to be the inner IP and port of the server
- in each of these cases, an entry is made in a table recording the
mapping (inner IP, inner port <-> PortNAT for external IP,
external port)
- this table to rewrite packets from the inside to be valid (routable)
on the internet, and packets outside outside to be delivered to the
correct host inside
- the hosts on the inside are configured to use the NAT box as their
default router, so they forward all their external traffic to the inner
interface of that box
Network Address Translation Examples
- NAT box with IPofficial = 1.2.3.4,
IPinside = 192.168.100.1
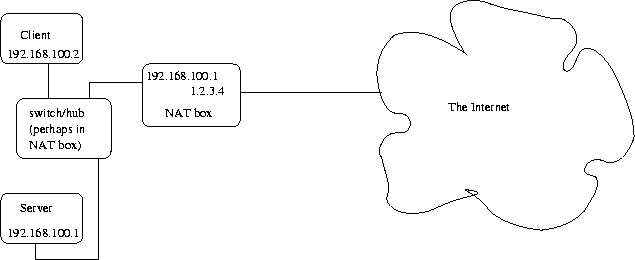
- client on the inside with IP = 192.168.100.102 sends to "next hop"
192.168.100.1 a packet with IP src = 192.168.100.102,
IP dst = 2.3.4.5, TCP src port = 4567, TCP dst port = 993 (IMAP over SSL)
- NAT box sends a packet to its next hop router with
IP src = 1.2.3.4, IP dst = 2.3.4.5, TCP src port = 4567, TCP dst port = 993
- TCP packets received by the NAT box with
IP src = 2.3.4.5, IP dst = 1.2.3.4, TCP src port = 993, TCP dst port = 4567
are rewritten to
IP src = 2.3.4.5, IP dst = 192.168.100.102, TCP src port = 993,
TCP dst port = 4567
- the inner TCP port may also be modified if necessary to avoid
confusion of two connections, e.g. another client connecting to TCP port
993 of 2.3.4.5 from its port 4567 would have its inner port changed
- a server on the inside with IP = 192.168.100.101, serving HTTP on port 80
- incoming packets received with any source IP and TCP port for port 80
of the NAT are rewritten to have destination IP 192.168.100.101
- a server on the inside with IP = 192.168.100.102, serving HTTP on port 80
might be configured to receive packets sent to the NAT's port 8080
- also functions as a firewall, discarding unsolicited packets
to any port that is not explicitly configured
- UDP functionality is similar, but since there are no connections,
requires caching and timing out of table entries
Nesting NAT boxes
- will the "inner" NAT box accept a non-routable IP as its "official" IP?
- if so, nesting should allow arbitrary use of NAT boxes to build
larger networks
- can the "inner" IP address of a NAT box be configured?
- if so, then the inner hosts will be able to access the outer hosts
Transport Layer
- TCP, UDP, demultiplexing, sockets/WinSock APIs
- headers, pseudo-header for end-to-end reliability
- reliable transmission
- flow control: stop-and-wait, sliding windows,
sequence number wrap-around, time-to-live
- congestion control: linear increase/multiplicative decrease
Data Link Layer
- framing, addresses, and access control
- wireless and Aloha
- Ethernet: header, hubs, switches, speed ranges, half and full duplex,
collision detection, binary exponential backoff
- learning bridges/switches, spanning trees, comparison of routing
and switching, wormhole routing
- serial lines, SLIP
ATM and Public Networks
- ATM:
- 53-byte cells (5+48)
- virtual circuits:
VPI, VCI identify connection, only have meaning locally to one link
- IP over ATM: virtual LAN (everything multicast to the nodes on
the LAN), Classical IP over ATM (CLIP, connection set up for each IP
destination, ATMARP)
- connection signaling, Quality of Service, adaptation layers (AAL-5)
- SONET: synchronous, 8000 frames per second
- Frame Relay: virtual connections, packet oriented
Networking Issues
- connectivity
- performance: bandwidth/throughput, latency/RTT
- error rate and correction: where do you put the redundancy?
- encryption, authentication, data encoding and compression
- network models: OSI, TCP/IP, ATM

